Time to Eliminate Those Security Blind Spots.
We discussed the importance of Continuous Threat Exposure Management and the differences between Manual pen tests Vs our Managed Threat Exposure Service powered by the cutting edge NodeZero™ security posture and exploitation solution. The question is what to do next.

Previously in Cyber Vigilance Techie Blogs…
We discussed the importance of Continuous Threat Exposure Management and the differences between Manual pen tests Vs our Managed Threat Exposure Service powered by the cutting edge NodeZero™ security posture and exploitation solution. The question is what to do next and how two different tools can empower each other to build a cohesive stategy.
Obviously, these assessments need to be carried out on a continuous basis to ensure that your organization isn’t vulnerable to new CVE’s or new hardware added isn’t exploitable.
There are 2 important steps which can be prioritised in any order that can improve your security posture and breach resilience drastically.
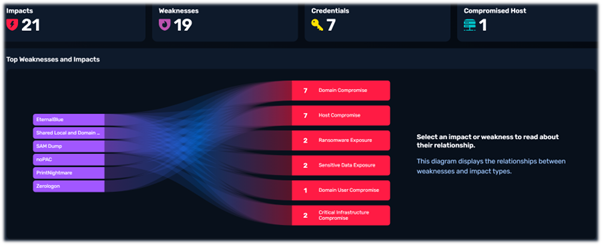
Keep your systems up to date with an automated patch management and vulnerability assessment tooling such as Vicarious. This solution can not only scan for the latest vulnerabilities but also apply automatic patching to hundreds of applications and many operating systems, even virtual patching for software that can not be updated to ensure these gaps are closed off to hackers. We will discuss Vicarius and how it can help you in more detail in a future blog post.

The 2nd or 1st step depending on your priorities is to keep attackers at bay by enforcing Identity and Access Management across the entire organisation, this is where the innovative Silverfort identity and security platform really excels and what we will be discussing in this blog.
Silverfort is very different to other IAM tools on the market today providing agentless real-time protection across the entire organisation by integrating with your existing IAM infrastructure, for example Active Directory and Entra ID. Silverfort has a unified dashboard giving you visibility into all access attempts and all identities in an instant. By analysing and risk assessing every user account in your environment you can control access immediately to anything malicious or suspicious. Imagine if you ran a pen test with this in place, it would not be able to get anywhere near as far into the network as it would be stopped in it’s tracks.
As well as controlling and monitoring accounts and their access you can replace existing MFA solutions with Silverfort's own MFA solution or simply choose one of your existing solutions like Microsoft or Okta (there are many) as the preferred MFA provider. The Silverfort MFA solution is different to anything that I have ever seen allowing you to enforce MFA at the command-line level and even for legacy applications. With MFA and Access management covered across the organisation any attempts to hack the network would be denied before any damage can be done.

There are obviously many more steps to completely securing your organization such as User awareness training, incident response planning and configuration management which we will cover off in future posts, in the meantime if you need any further information or just an honest chat around security controls you know where we are.

Chris Faulkner
Senior Cyber Security Consultant
Get safer now
See how Managed Threat Detection can make a difference for you. No obligation free trial.
©2025 Cyber Vigilance
Powered by Disruptive
Naggs Stable, Old Portsmouth Road, Guildford, Surrey, England, GU3 1LP