Offensive Testing to Continuous Detection with Tripwires
Horizon3.ai Redefines Detection with the Next Generation of NodeZero Tripwires
Horizon3.ai Redefines Detection with the Next Generation of NodeZero Tripwires
In the relentless arms race between attackers and defenders, one thing remains constant: speed matters. The sooner you detect an intruder, the less impact it has. With its latest innovation, Horizon3.ai has taken that principle to the next level — unveiling Active Directory Tripwires, a powerful expansion of its NodeZero platform that combines offensive testing, deception, and real-time detection into a single seamless capability.
These new tripwires represent a significant shift in how organisations can defend against identity-based attacks — one of the most common and damaging threat vectors in today’s environments.

From Offensive Testing to Continuous Detection
Horizon3.ai’s NodeZero has long been known for its autonomous pentesting capabilities—continuously probing environments to uncover exploitable weaknesses before attackers do. The introduction of Tripwires built upon this foundation by planting deceptive assets – such as fake credentials or files – precisely where vulnerabilities existed.
Unlike traditional honeypots, Tripwires are not randomly distributed; they’re placed intelligently along real attack paths revealed during pentests. This ensures high-fidelity alerts and minimal false positives — every trigger is a sign of genuine malicious activity.
Now, with the release of Active Directory (AD) Tripwires, Horizon3.ai has moved deception into the heart of enterprise identity infrastructure.

What’s New: Active Directory Tripwires
The new AD Tripwires are designed to detect attacker activity targeting the identity layer — where privilege escalation, lateral movement, and persistence commonly occur.
1. Decoy Accounts that Blend In
NodeZero can now create a small number of realistic decoy user accounts that mimic legitimate identities within Active Directory. These accounts use believable naming conventions and typical permissions to blend naturally into your environment.
If an attacker interacts with one — for example, by attempting authentication, enumerating attributes, or requesting Kerberos tickets — an immediate, high-confidence alert is triggered.
2. Detection of Advanced Identity Attacks
AD Tripwires are engineered to detect several high-value tactics, including:
- Kerberoasting – When an attacker requests service tickets for decoy Service Principal Names (SPNs).
- AS-REP Roasting – Triggered when pre-authentication is bypassed on decoy accounts.
- Account Enumeration – When attackers query AD for user details or credentials embedded in descriptions.
Each interaction generates rich contextual data — detailing the decoy targeted, the method used, and the path of exploitation — giving analysts immediate visibility into attacker intent.
3. Built-in Logging and SOC Integration
To catch these events, Horizon3.ai’s AD Tripwires integrate directly with Windows event logs, monitoring for key authentication events (4625, 4768, 4769, 4771, 4776) involving the decoy accounts. Alerts feed seamlessly into your existing SIEM or SOAR stack, ensuring rapid triage and automated response.

Why It Matters
Most modern cyber-attacks exploit Active Directory at some point in the kill chain. Once inside, attackers use legitimate tools and credentials to escalate privileges — often without raising traditional alerts.
By introducing Tripwires at the identity layer, Horizon3.ai has effectively built an early-warning system that catches attackers the moment they start probing AD.
Key benefits include:
- Reduced Dwell Time – Tripwires provide instant visibility into malicious AD activity.
- High Signal-to-Noise Ratio – Alerts are triggered only by genuine adversarial behaviour.
- Validation of Detection Pipelines – Teams can test and verify whether their SOC would detect real identity abuse.
- Operational Synergy – Integrates offensive insight directly into defensive monitoring, aligning red and blue teams under one platform.
Making the Most of AD Tripwires
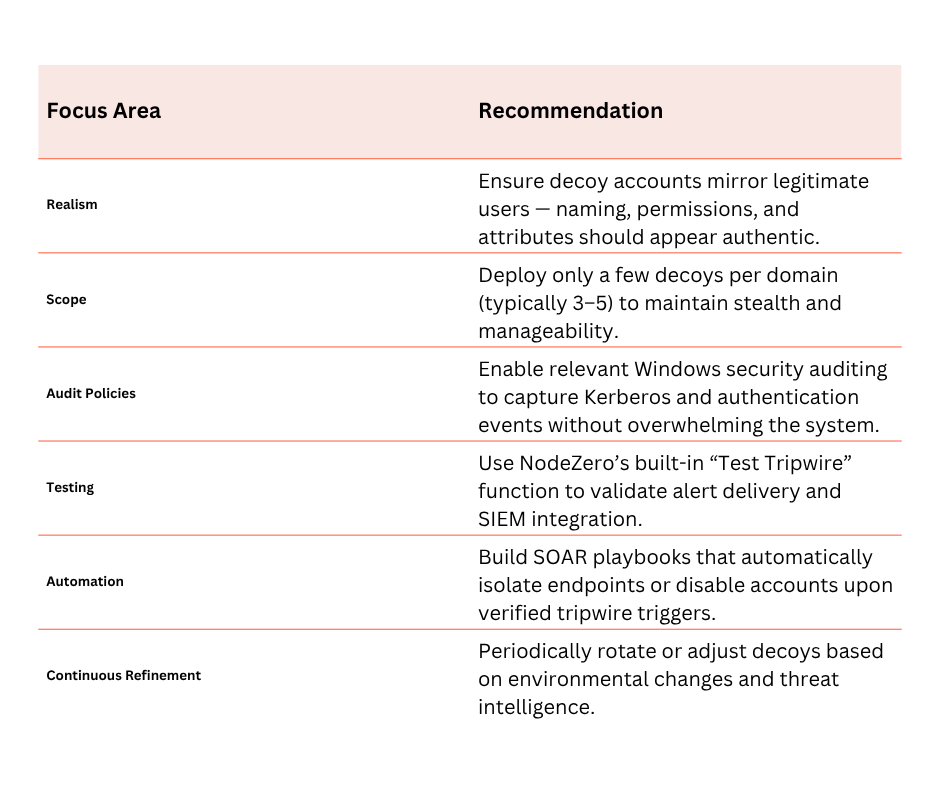
To fully harness the power of Horizon3.ai’s new Tripwires, organisations should follow several best practices:
A Real-World Example
Imagine an attacker gaining a foothold through a vulnerable endpoint. They begin enumerating Active Directory users to identify privileged accounts. When they touch a decoy account planted by NodeZero — perhaps querying its description or requesting a service ticket — the tripwire activates.
Within seconds, the SOC receives a contextual alert that pinpoints the attacker’s IP address, the decoy triggered, and the technique used. What could have remained invisible for weeks is now actionable in real time.
This proactive detection drastically shortens the attack chain, allowing defenders to respond before any real damage occurs.

The Bigger Picture: Offence-Informed Defence
Horizon3.ai’s latest evolution underscores a broader industry trend: the convergence of offensive security and defensive operations. By leveraging autonomous pentesting data to strategically deploy tripwires, NodeZero turns attack intelligence into living defensive instrumentation.
This approach transforms the defender’s posture from reactive to anticipatory — not just waiting for alerts but actively shaping where and how they appear.

Final Thoughts
The new Horizon3.ai Active Directory Tripwires represent more than a product update — they signal a shift toward continuous, offence-informed detection.
By embedding deception into identity systems, Horizon3.ai empowers security teams to detect attackers earlier, respond faster, and validate their defences with real-world precision.
In a world where identity is the new perimeter, this innovation could redefine how we think about visibility and resilience inside the enterprise.
Click "More Info" to discover the full Horizon3.ai platform, and book in a demo.
Get safer now
See how Managed Threat Detection can make a difference for you. No obligation free trial.
©2025 Cyber Vigilance
Powered by Disruptive
Naggs Stable, Old Portsmouth Road, Guildford, Surrey, England, GU3 1LP