Testing Your EDR Effectiveness with Horizon3 NodeZero!
Learn more about the free EDR Healthcheck!
In today’s Cybersecurity landscape Endpoint Detection and Response (EDR/XDR) solutions are as important as they have ever been, especially with ransomware and other malicious attacks still on the rise. These solutions promise to detect, block, and contain threats before attackers gain a foothold. Unfortunately, without constant testing most organizations don’t know how effective their EDR really is. The usual checks like confirming agents are installed, communicating and up to date create a false sense of security. These checks don’t answer the most important question: Could attackers bypass your EDR in a real-World attack?
NodeZero from Horizon3.ai changes that by providing evidence-based validation of EDR performance in live environments. Let’s look at how you can use NodeZero to test and improve your EDR effectiveness.
Why is it Important to Validate your EDR?
Attackers are increasingly using credential-based attacks, lateral movement, and privilege escalation techniques that often bypass signature-based or misconfigured behavioral detection. A huge percentage of successful EDR bypasses use stolen credentials, not software exploits. Once inside, the attackers can complete critical actions like data collection within minutes. Without validating, your EDR security blind spots remain hidden, EDR misconfigurations are left unresolved, and your IT team assume your endpoints are safe without having the evidence to prove it.
Welcome to NodeZero Endpoint Security Effectiveness (ESE)
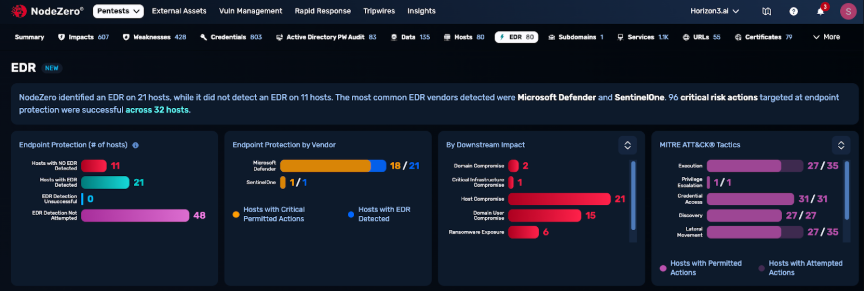
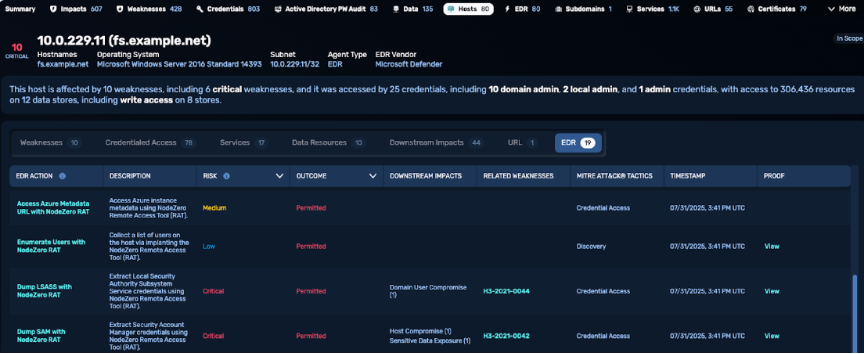
Endpoint Security Effectiveness (ESE) gives you visibility into how your EDR performs during a NodeZero Internal pentest. Once configured, this feature transforms your pentests into a controlled EDR evaluation. Safely simulating real-World attack behavior, such as remote command execution and credential dumping on connected endpoints without interrupting daily operation. Each blocked and permitted action is mapped to a MITRE ATT&CK tactic and recorded in detail for review.
During a pentest, NodeZero attempts attacker behaviours on target hosts and records whether the EDR on the host blocked or permitted each action. The results are then published in the “EDR” tab of the pentest results page. NodeZero can detect over 40 EDR vendors including SentinelOne, Crowdstrike, Microsoft Defender. We can provide a full list of supported vendors.
The requirements to ensure NodeZero can access the hosts and test EDR performance are simple, see below:
- The host(s) are running Windows (Linux is not currently supported)
- NodeZero has admin level credentials to the host (this could be a local admin, a domain user with admin privileges or a domain admin) with remote access to WMI (port 135). In some cases, NodeZero is still able to analyse the EDR on a host by exploiting a vulnerability on the host or an admin-level credential.
- If a domain credential is being used, the domain controller needs to be in scope of the pentest. All of this can be added using template for the pentest.
- The NodeZero runner can also be configured with Auto-injected credentials that are stored securely just on the runner and can be selected in the pentest template.
What ESE Provides you with
- Coverage Overview - Which hosts have EDR deployed, which don’t, and where detection failed.
- Vendor Breakdown - Performance comparison across EDR vendors.
- Proof if your EDR is alerting you to attacks or not.
- Action Analysis - Which NodeZero actions were blocked, alerted, or permitted.
- Downstream Impact - Potential consequences if actions were allowed (e.g., credential theft, domain compromise).
- MITRE Mapping - Every permitted action tied to ATT&CK techniques for better policy tuning.
-
How to Test EDR Effectiveness with NodeZero
As a NodeZero Service provider Cyber vigilance can configure and run these assessments for you either during a POV or after the purchase. Please contact us for details.
If you are self-managed and want to give this a go, the steps are straight forward:
1. Configure the Scope and Deployment
- Deploy a NodeZero Runner inside your network for internal pentests.
- Ensure there are domain controllers and high-value assets in the scope.
- Inject admin-level credentials, this allows NodeZero to fully analyze EDR performance.
2. Run an Internal Pentest
- Configure the test in the NodeZero portal.
- Include as many exploitation tools as possible such as the Remote Access Tool.
- NodeZero will attempt attacker behaviors and record EDR responses in real time.
3. Analyze Results
- Navigate to the EDR tab in the pentest results.
- Review:
- Hosts with EDR detected / not detected.
- Actions that were permitted.
- MITRE ATT&CK Tactics.
- Drill down into specific hosts for detailed forensic evidence.
4. Tune and Validate
- Use this information to adjust EDR policies and integrations.
- Run the test again NodeZero to validate this is key to cyber resilience.
Why NodeZero Stands Out
Unlike traditional breach and attack simulation tools or manual red pentesting, NodeZero offers:
- Agentless Setup.
- Minimal spec VM for the runner.
- Reverse engineered attacks to be production safe.
- Comprehensive reports mapped to MITRE ATT&CK.
- Easy to follow fix actions reports.
- 1-Click Verify to validate fixes immediately after policy changes.
Final Thoughts
Testing your EDR effectiveness isn’t an optional task, it’s essential. Horizon3’s NodeZero gives you the proof you need to move from assuming you are protected to ensuring you are protected. By adding ESE into your security testing policies, you can uncover many more blind spots, tune your EDR configurations, and prove that your investment is actually doing what it says on the tin.
Book in your free assessment now!

Chris Faulkner
Senior Cyber Security Consultant, SentinelOne Paladin
Get safer now
See how Managed Threat Detection can make a difference for you. No obligation free trial.
©2025 Cyber Vigilance
Powered by Disruptive
Naggs Stable, Old Portsmouth Road, Guildford, Surrey, England, GU3 1LP